Closing the Cyber Attack Gap with AI
This has great value in the cyber world. A semantic graph for cyber threats can be produced by using information and concepts found in standard information sources, such as MITRE ATT&CK and NVD CVE. Attack techniques can be analyzed to define the “requirements” of the attackers. By combining a semantic graph of cyber threats with a graph describing features of an organization’s IT systems, the reasoning system can deduce what information is needed to enable the technique and build a “virtual attacker” that can explain how, in principle, to attack an organization. This tells the organization how and where they are open to attack—without the need for other, often manual means of uncovering cyber exposures, such as penetration testing.
Once there is an accurate description of the IT systems of an organization, the connectivity between the systems and the description of the system’s identity and access information, the reasoning system can build specific attack scenarios for that organization—just as a real attacker would. If we then add to the system semantic information about defenses (mitigations) as they are defined by MITRE D3f3nd, the system can suggest ways to reduce the risks from those attacks.
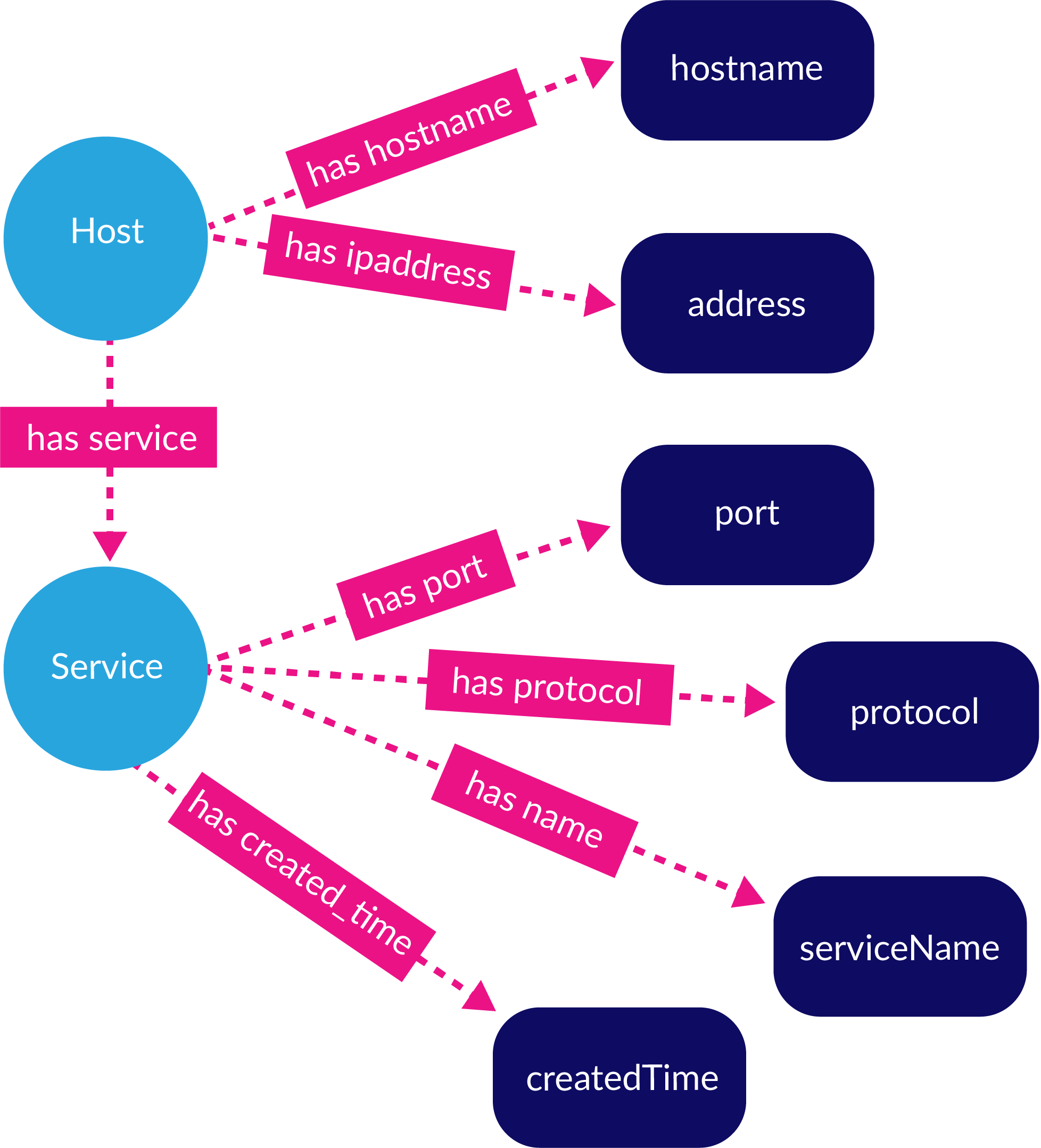
Figure 1: A simple semantic graph describing basic concepts from the IT relevant to attackers and defenders
For these reasons, machine reasoning is particularly suitable as a system for assessing an attacker’s ability to succeed in attacking the organization without conducting the attack. It also enables the assessment of organizational resilience to prevent or minimize the loss from cyber attacks.



















